WIN32 SALITY REMOVAL TOOL FREE DOWNLOAD
It alters the safe mode functionality to ensure it remains on the compromised computer. Remember to scan any removable or portable drives. AT tries to download files from remote servers to the local drive, then decrypts and runs the downloaded files. Free scanner allows you to check whether your PC is infected or not. The following can indicate that you have this threat on your: 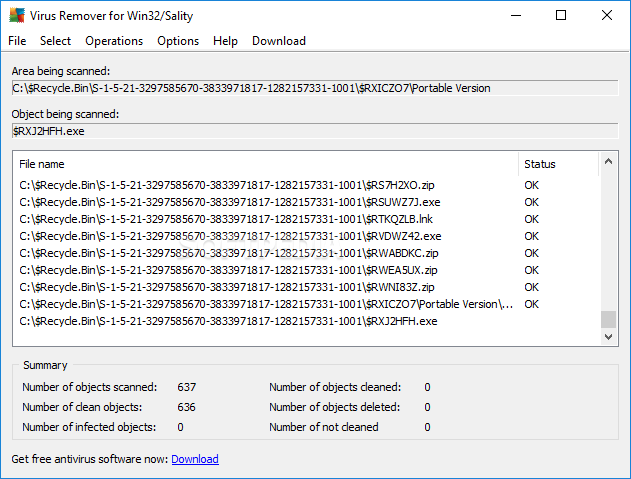
| Uploader: | JoJoran |
| Date Added: | 21 January 2007 |
| File Size: | 42.64 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 73741 |
| Price: | Free* [*Free Regsitration Required] |
Disable the autorun feature to prevent dropped files from running automatically when a network drive is opened. Among these activities is the decentralized peer-to-peer network P2P that W At that time, W Performing a full system scan How to run a full system scan using your Symantec product 2.
There are different types of Sality viruses around. If this free removal guide helped you and you are satisfied with our service, please consider making a donation to keep this service alive.
Some anti-virus providers created tools that are specifically designed to remove Sality virus. This threat might make lasting changes to your 's settings that won't be restored when it's cleaned.
Virus:Win32/Sality.AT
PC Certain security-related applications, processes or services might suddenly close, end, or not run at all. AT tries to download files from remote servers to the wni32 drive, then decrypts and runs the downloaded files.
If write access is not required, enable the read only mode if the option is available. But more importantly, we will also offer you an effective solution for the removal of Win32 Sality Virus. Sality will not inject into processes that belong to the system, the local service or the network service.
Users should disable AutoPlay to prevent automatic launching of executable files on removable drives.

The goal of the complex code is to make analysis more difficult for researchers to see the real purpose and functionality implemented in the code. Thus, finding it and reverting the changes is an extremely complicated task that should only be practiced by trained IT specialists.
Win32 Sality Virus Removal (June 2019 Update)
ermoval We recommend downloading SpyHunter to scan for malicious programs, which may have been installed with it. AT SFC does not infect files protected by or if the file name starts with one of the following strings:.
Blocking the following default port at network perimeter will help to reduce the risk to your computer: They can be after certain files, which they can copy and send to sa,ity masters. Registry Editor Registry Editor.
In addition to infecting local and remotely shared executable files, W This threat tries to use the function to spread via removable drives, like flash drives. The virus seeks other target files by reading file names found in the following registry subkeys: Not to mention that it could even destroy your OS or just erase everything from it, leaving you with a completely blank canvas.
Download Win32/Sality Remover® latest free version | Downloadcom
Therefore, if you are unsure of your computing skills or would prefer to have professional software cover you, we can also provide you with that remocal well. Some users are not aware of certain things that need to be done in order to protect themselves, while others simply neglect adequate security means. One of the most important toool is to obtain reputable security software.
The malicious threat is considered to be one of the most complex and powerful malware ever created. Ask us a question Post a comment.
Microsoft You should also run a full scan.
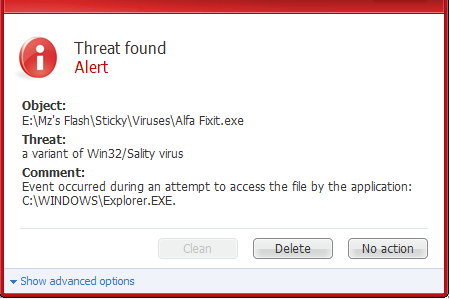
It replaces the original host code at the entry point of the executable to redirect execution to the polymorphic viral code, which has been encrypted and inserted in the last section of the host file. Depending on the type of malware, various tools can be used.
This means it can go online without being blocked.
A full scan might find other, hidden malware. If you are hacked, there will be a bunch of other IPs connected to you at the bottom.


Comments
Post a Comment